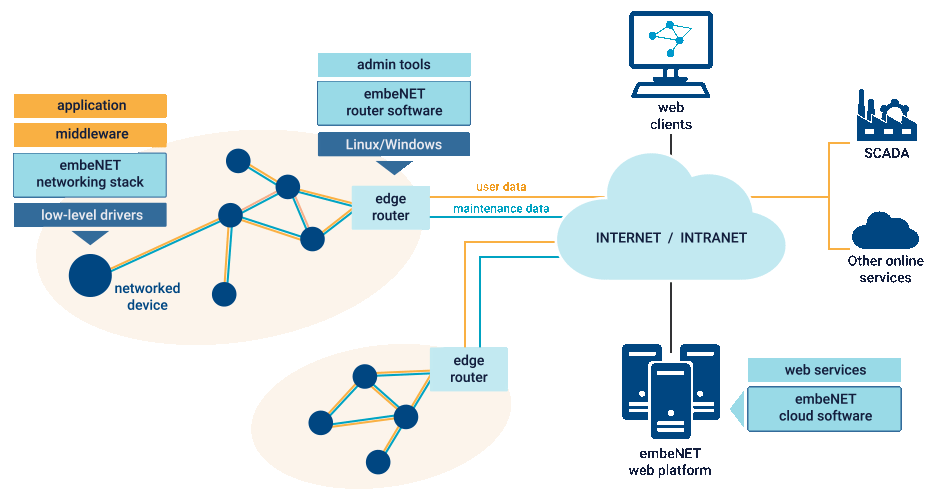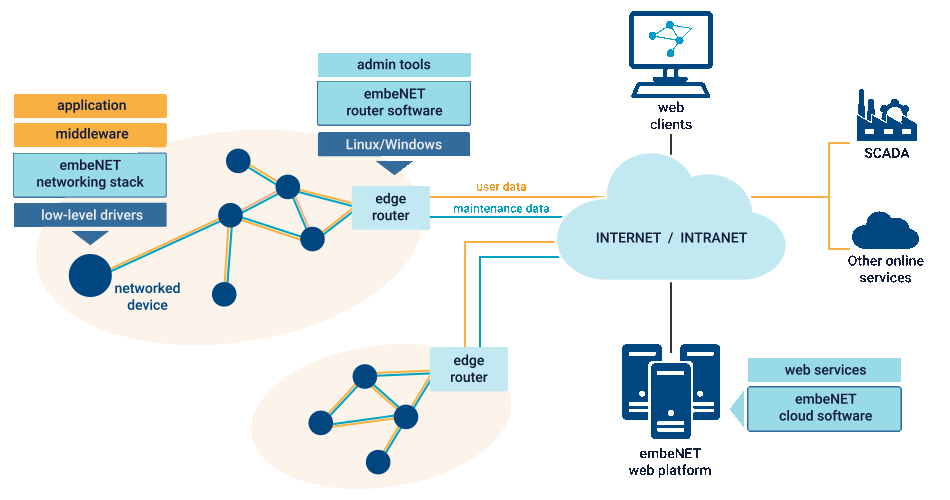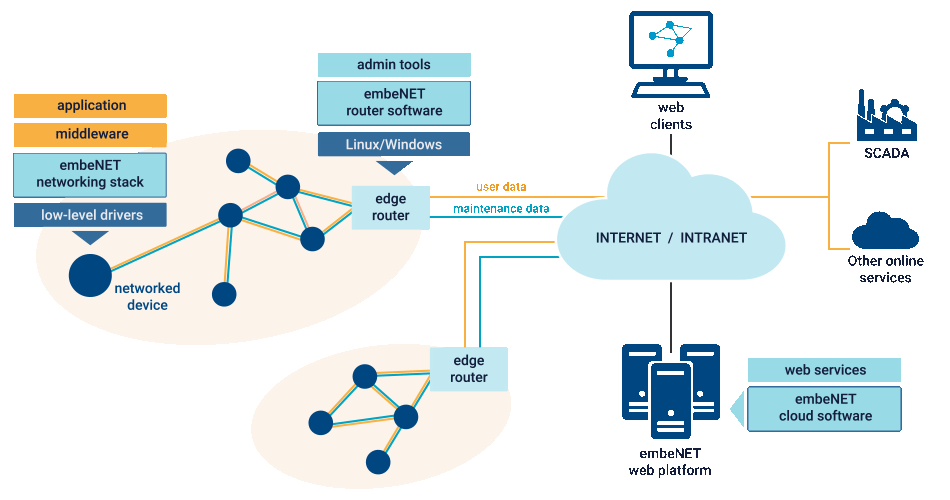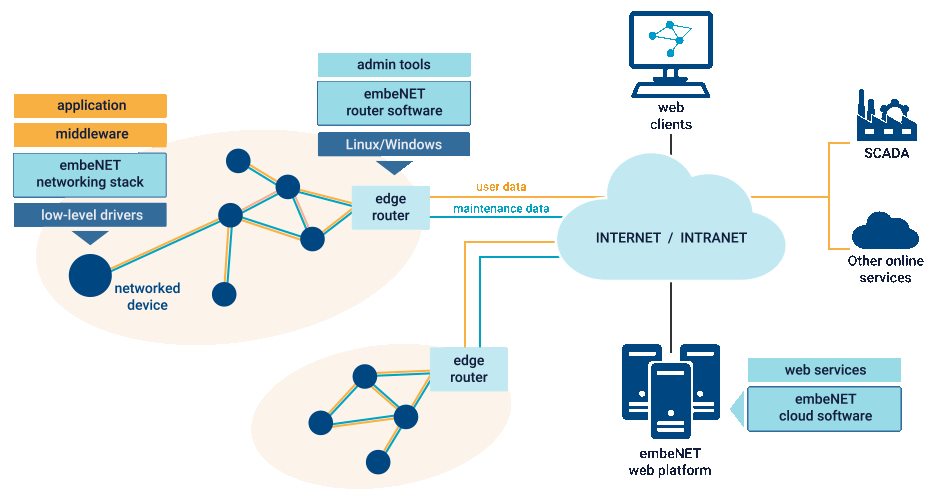
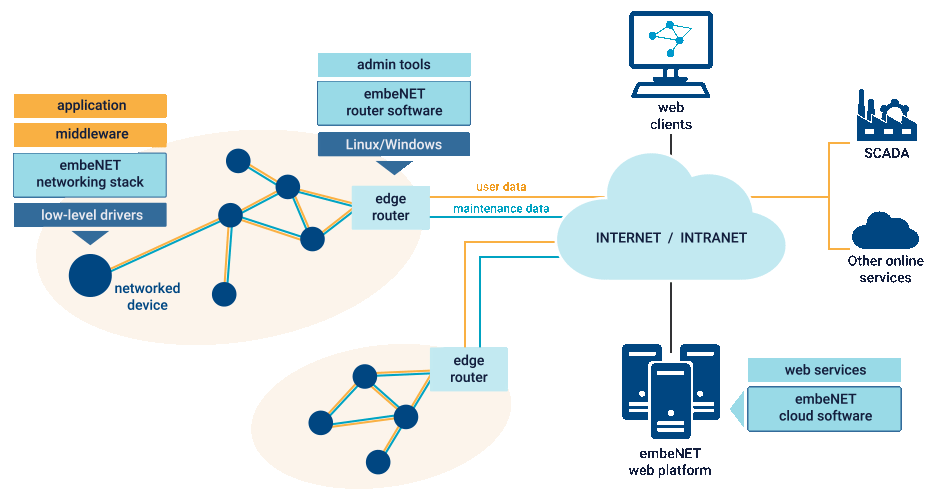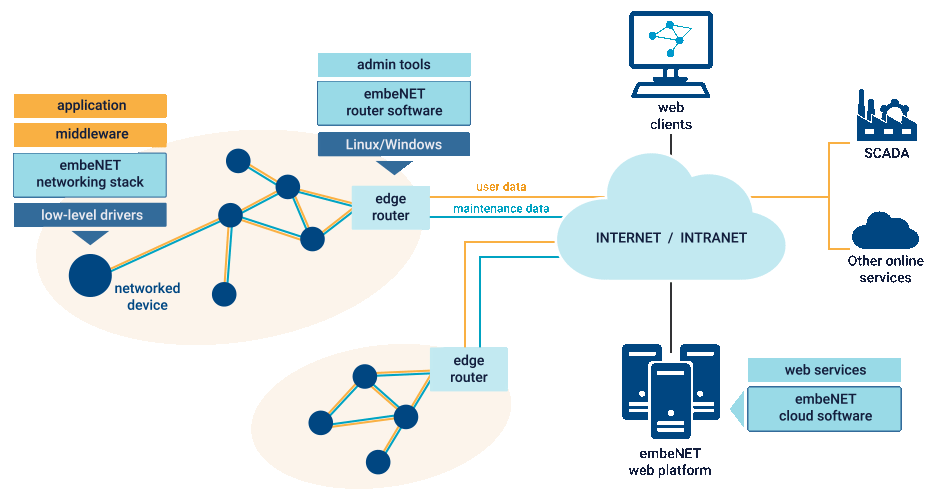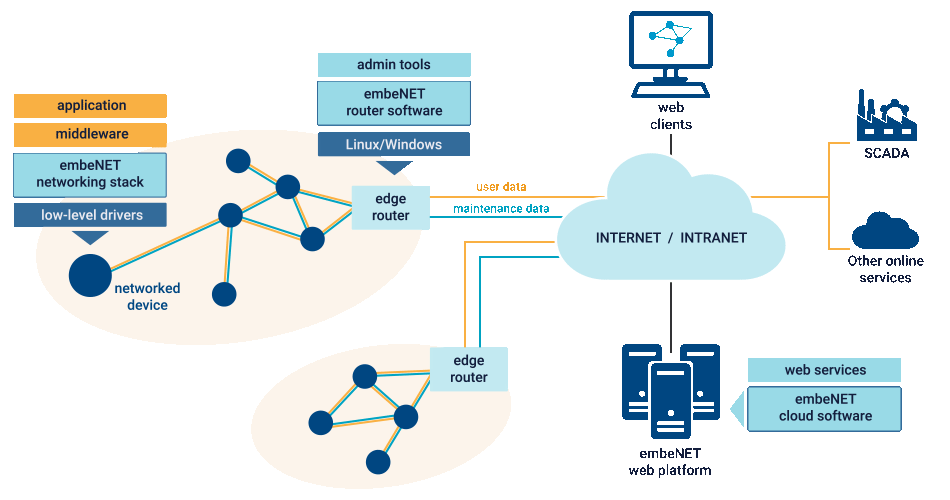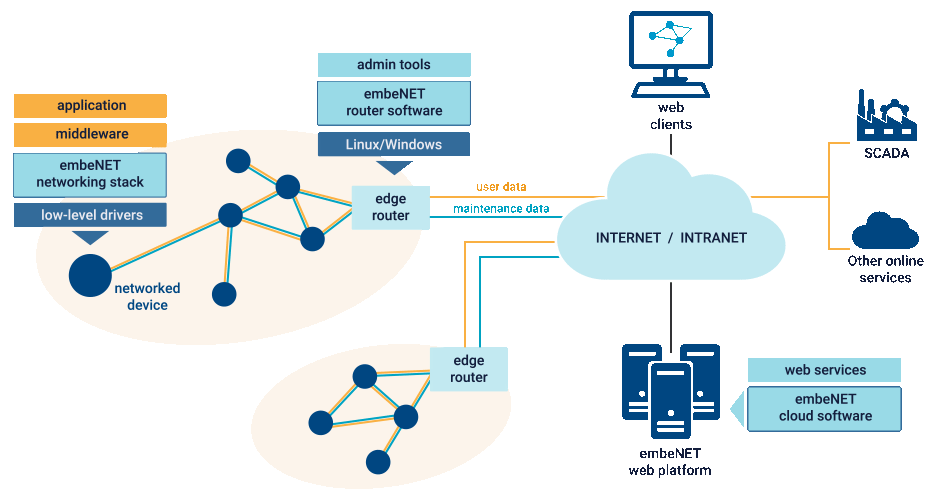
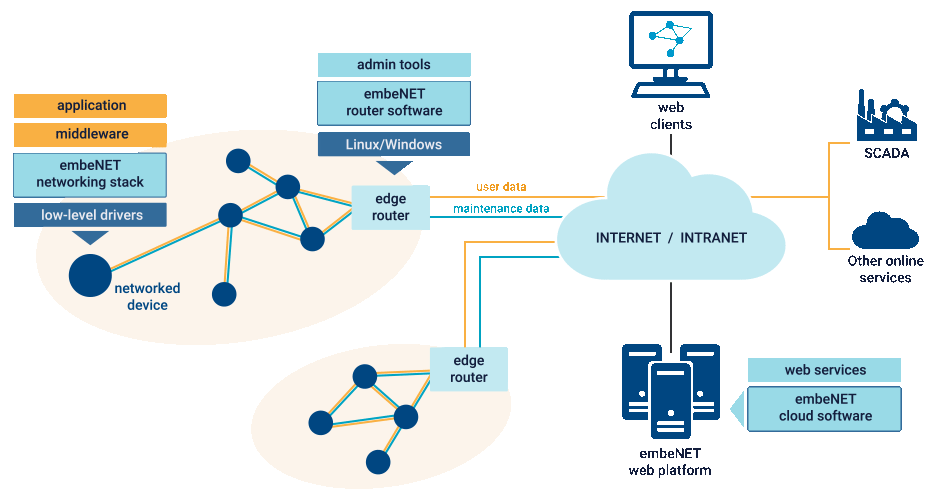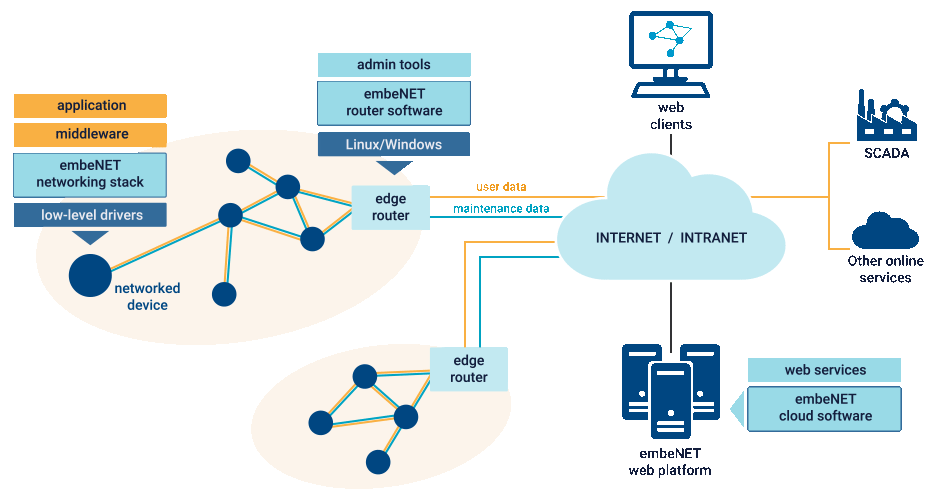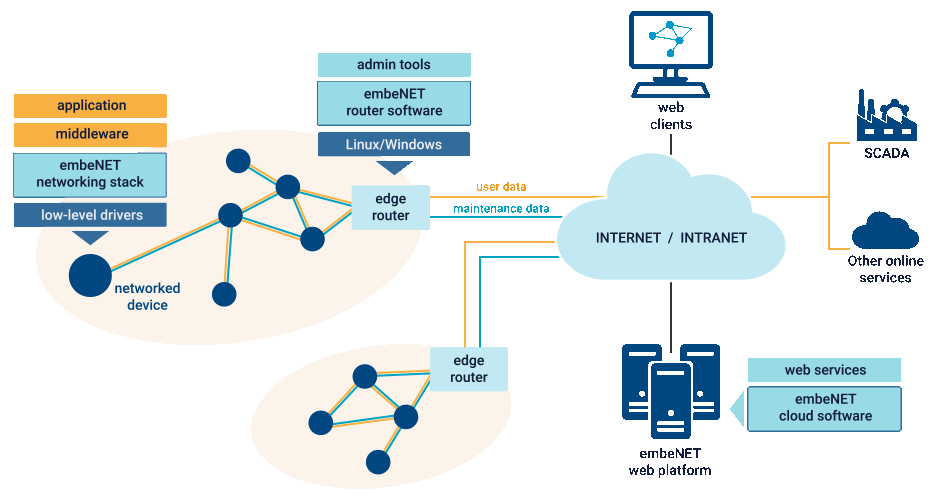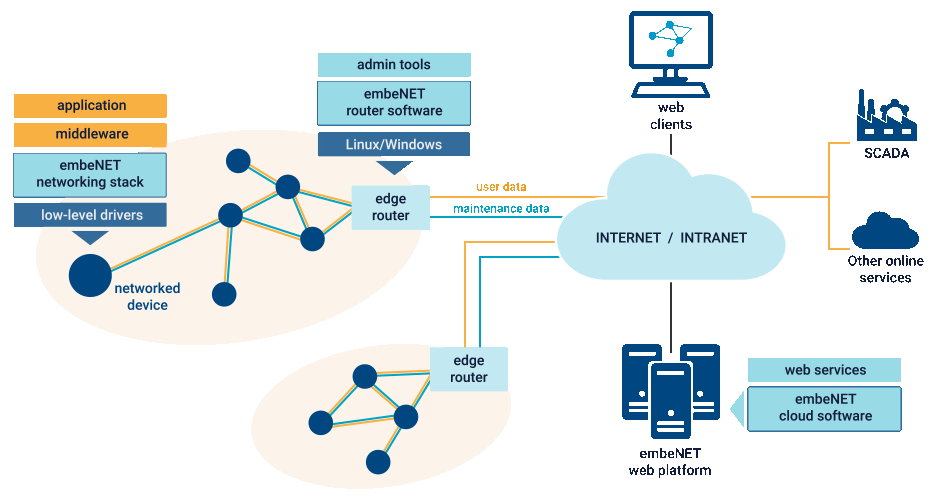
The embeNET networking stack implements Low-Power and Lossy Network (LLN) communication that runs on various resource constrained devices. We support 2.4 GHz and subGHz bands. Appropriate operating band can be chosen depending on your requirements. The usage of popular modulation schemes within PHY layers makes it possible to use popular and low-cost radio transceivers which significantly reduces the overall product cost. The whole process of joining nodes to the network, routing and topology reconfiguration takes place automatically. The highest stack layer which is designed to cooperate with your application is based on the well-known UDP transport layer. As a result communication between applications takes place via addressable sockets which is a mature and well-regarded technology.
MAC and PHY layers in the embeNET stack are implemented in conformance with IEEE802.15.4e-TSCH standard. It is a proven technology dedicated for industrial deployments, giving high quality and robust connectivity even in harsh environmental conditions. Furthermore, networked devices can run for years being battery powered.